- 404
- Home
- Remote Administration
- Employee Monitoring
- Information Security
- Features
- Live Employee Desktop
- Employee Internet Monitoring
- E-mail monitoring
- Keystroke Monitoring
- File Activity Monitoring Software
- Printed document tracking
- Optical Character Recognition (OCR)
- Smart rules & alerts
- Network activity monitoring
- App usage/application monitoring
- Instant Message Monitoring
- Remote Desktop Control
- Active vs. Idle Time Analysis
- Employee Productivity Tracking
- Linux terminal capture
- Nonproductive Activity Reporting
- Custom reports
- Session Recording & Metadata
- User Card
- Screen Capture
- Web-cam snapshots
- USB device control
- Data Leak Prevention (DLP)
- Voice communication recording
- File Scanner
- Software and Hardware Inventory
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Pricing
- Request demo
- Solutions
- Purchase
- Demo request
- 404
- index
- Remote Administration
- Employee Monitoring
- Information Security
- Features
- Insider Threat Detection & Prevention
- Remote Employee Monitoring
- Privileged User Monitoring
- Productivity optimization
- Third Party Vendor Management
- Compliance Management, Auditing & Monitoring
- Cases
- GDPR Compliance
- For HIPAA
- For Legal
- Government & Public Sector Cyber Security
- PCI DSS Compliance & Certification
- General Data Protection Regulation (GDPR)
- Energy & Utilities Sector Cyber Security
- For Financial Sector
- Retail & Ecommerce Cyber Security
- About Us
- Why Us?
- Partners
- White Papers
- Support
- Pricing
- Request demo
- Solutions
- Purchase
- Demo request
Energy & Utilities Sector
Cyber Security
Cyber Security
Identify, Protect, Detect, Respond & Report on Healthcare Data Breaches
Request demoStaffCop for the Energy & Utilities Sector
The energy and utilities industry has historically been inundated with threats from external sources including hackers, environmental activists, and industrial and state espionage. As a result, the industry has set security as their top priority. Thanks to their efforts, it has become more difficult for an outside attacker to penetrate critical energy and utilities systems. That’s good news.
However, what’s not good is, the criminals have now turned to enlist insiders, ie employees and contractors in these organizations to gain access using various methods like social engineering, id theft/ impersonation, baits or collusion. Being insiders, these users already have access to critical systems, sensitive data and IP, and can cause more damage than an outsider. While the cost of insider-caused incidents varies by industry, energy and utilities remains one of the highest - spending tens of millions in average to contain the damage caused by such threats.
The energy & utilities sector is also highly collaborative where larger companies utilize contractors, outsourcing partners and suppliers for offshore operations, exploration, distribution, analysis and legal matters. A third-party can easily expose the company to great financial, IP and other risks either accidentally or intentionally. There are also consulting firms working with multiple oil and gas companies providing design and engineering services who need to share confidential and sensitive information such as reservoir data, seismic reading, future exploration sites etc. These firms are often targeted by competitors, criminals, and even their customers for the invaluable trade secrets.
In an industry where employees, vendors and contractors have access to critical infrastructures, privileged information or intellectual property on a regular basis, securing the resources and information is crucial for the industry as well as for the safety of the citizens utilizing their products and services.
StaffCop Combines Insider Threat Detection and Data Loss Prevention into a Single Integrated Solution for Energy & Utilities Companies
With StaffCop, energy and utility companies can monitor and protect critical infrastructure from malicious or accidental insider threats, safeguard information of future plans, trade secrets, IP and customer information and meet compliance goals for NERC, FISMA, ISO 27001 with its powerful policy and rules engine, forensic audit and reporting features. Here are a few expels of what an energy or utility company can achieve with StaffCop’s unified User Activity Monitoring, Threat Detection and DLP platform:
Gain operation-wide visibility into the user activity of critical infrastructure assets for both OT and IT systems including endpoint, servers, terminals, back/front office systems.
Prevent stealing of high value intellectual property like survey and testing data, drilling and logistics information, site plans, bid for drilling rights and more.
Extend monitoring and control to partners, vendors, consultants and other third-parties for secure collaboration on joint-venture projects.
Restrict modification of system software, access elevation, malicious code execution and other potential harmful activity by privileged users.
Protect customer information, employee privacy and corporate data.
1
Monitor Critical Systems and Users
StaffCop monitors all user activity over endpoints, servers/terminal servers, network and cloud for 22+ system objects like: websites, applications, emails, files even on-screen content (OCR) in real-time
2
Detect Insider Threats
Intelligent behavior analysis can detect malicious activity and anomalies that indicate deviation from normal behavior. Use the powerful Policy & Rules Editor to create rules to define what constitutes insider threats. StaffCop then takes immediate actions like warn, block, lockout user or take remote control of a system when rule violation is detected.
3
Discover & Categorize Sensitive Data Automatically
Deep content inspection in both structured and unstructured data accurately identifies classified and confidential information. StaffCop also supports real-time content discovery with advanced OCR, digital fingerprinting and tagging.
4
Safeguard Data and IP
Protect confidential design, production and exploration plans, shield private employee and corporate information, trade secrets, IP and other sensitive information from falling into the wrong hands.
5
Enable Secure Collaboration
Use a combination of terminal servers, VMWare or Citrix servers to allow your partners collaborate on projects in a secure sandbox. Record their activates, restrict access or take control of the server in case of an incident keeping rest of your operation immune from disruption.
6
Conduct Cybersecurity Risk Assessment
Dynamic risk scoring and vulnerabilities scanning identifies at risk employees, policies and system resources. Detect, analyze and prioritize security gaps before they can be exploited.
7
Manage Compliance
Conform with security and regulatory standards like NERC, FISMA, FERC, ISO 27001, GDPR etc. Speedup standard implementation with flexible Policy & Rules editor and various monitoring and reporting features.
8
Protect Your Operations from 3rd-Party Threats
Monitor third party vendors, contractors and consultants who have access to your critical systems to prevent sabotage or data theft.
9
Investigate Incidents with Forensics and Audit
Implement training and awareness programs with Session Recording & Playback and customized rule violation messages.
10
Coordinate Security Orchestration for Rapid Response
Integrate StaffCop with Intrusion Detection/Prevention Systems (IDS/ IPS), Access Control, Threat Analytics and SIEM systems. Create a cyber security perimeter across your stores, supply chain network and corporate offices. Share threat intelligence and coordinate response with analyts, CSO, MSSP and security teams.
Industry Statistics Show the Need for Privileged User Activity Monitoring
Security is a top concern among utilities
A survey of 600 electric utility executives found that cyber and physical security was the most pressing concerns for them. Source: UtilityDive.
72% Agree Cyber & Physical Security is Important or Very Importan
Energy is one of the most targeted critical industry
The U.S. energy sector, which includes the oil, natural gas, and electricity subsectors, is one of the most highly targeted critical infrastructure sectors. Source: DHS.
59% Cyber Incidents are Related to U.S. Energy Sector
Insiders are the top threats in the oil & gas industry
In a survey of OT experts, 65% said the top cybersecurity threat was careless insider and 15% said malicious insider. Source: Ponemon & Symantec.
65% Negligent Insider
15% Malicious Insider
Insider threats cost energy & utilities companies millions
Companies in energy and utilities incurred an average costs of $10.23 million in insider threat related incidents in 2018. Source: Ponemon & ObserveIT.
$10M+ Cost of Insider Threats for Energy & Utilities
Teramind Helps Energy & Utilities Companies Protect Sensitive Data
Energy
– Exploration, survey, seismic and other research data.
– Process flow, pipeline flow diagram, engineering designs. – Oil/gas drilling data like prospecting related terms, confidential/CB well list, Coalbed data etc.
– Business plans, legal data.
– Process flow, pipeline flow diagram, engineering designs. – Oil/gas drilling data like prospecting related terms, confidential/CB well list, Coalbed data etc.
– Business plans, legal data.
Critical infrastructure / utilities
– Distribution plans, software design documents, SCADA terms.
– Vendor Contracts.
– Business plans, legal data.
– Customer Data, Personally identifiable information (PII), Consumer-specific Energy Usage Data (CEUD), Customer proprietary network information (CPNI).
– Vendor Contracts.
– Business plans, legal data.
– Customer Data, Personally identifiable information (PII), Consumer-specific Energy Usage Data (CEUD), Customer proprietary network information (CPNI).
Corporate data
– Business processes and strategic plans.
– Price/cost/supplier/customer lists.Source code, formulas, patents and other type of IPs.
– Acquisition plans, M&A announcements, legal documents and other confidential matters.
– Payroll, accounting and financial data.
– Price/cost/supplier/customer lists.Source code, formulas, patents and other type of IPs.
– Acquisition plans, M&A announcements, legal documents and other confidential matters.
– Payroll, accounting and financial data.
And more...
– Billing/invoice, tax/VAT, GST/HST, enrollment and payment related data.
– GDPR special data categories (trade union data, biometric, geo location).
– For Official Use Only (FOUO), Confidential and Protected file tags.Federal
– Tax Information (FTI), Covered Financial Information (GLBA) etc.
– GDPR special data categories (trade union data, biometric, geo location).
– For Official Use Only (FOUO), Confidential and Protected file tags.Federal
– Tax Information (FTI), Covered Financial Information (GLBA) etc.
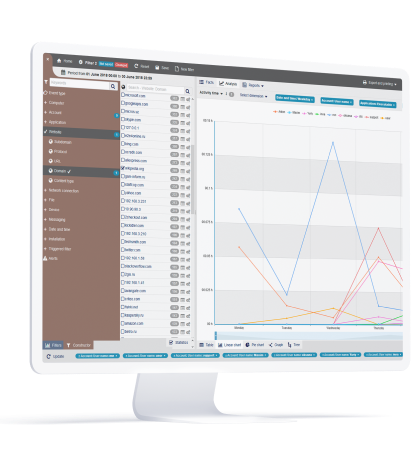
Real-Time Visibility and Control
StaffCop visually records every action that a user makes on your Operation Technology (OT) and IT systems including endpoints, servers/terminal servers, network and cloud, DMZ for 22+ system objects like: web, apps, email, file transfers, etc. Uncover what your employees are up to both online and offline. Each object can be configured to take into consideration what needs to be monitored and who has access to the monitored records. You can specify who you want to monitor, how much you want to monitor, when and for how long. This allows for instant administrative oversight in respect to all user activity while complying with any privacy requirements.
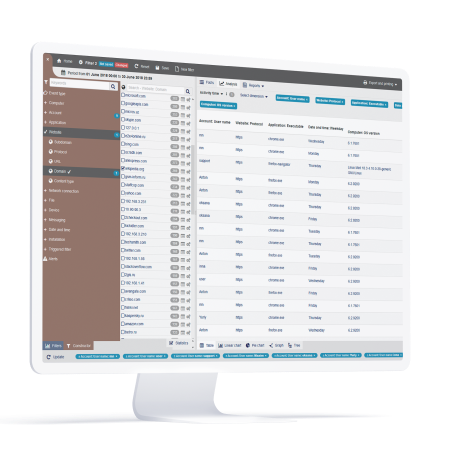
Automated Data Discovery and Classification
StaffCop has built-in templates for many classified and unclassified data types to protect your customer data, IP and other sensitive information. Custom data types easily be created using flexible regular expression (RegEx) and natural language definitions. Combine OCR and fingerprinting with multiple logic, file origin, file properties and data content to discover and protect confidential exploration and production data, engineering and technical design, source codes, contract etc.

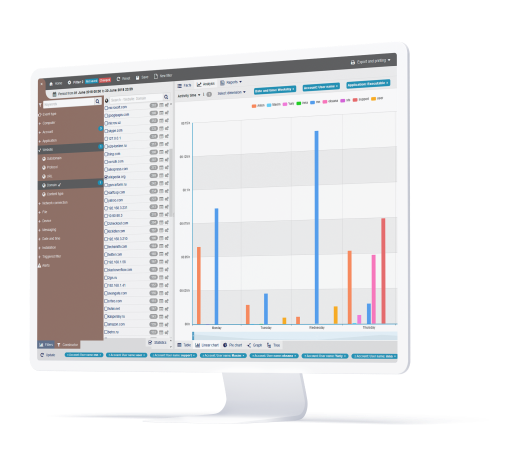
Powerful Policies and Rules Engine
The core of the StaffCop platform is its automation. StaffCop comes with hundreds of pre-defined policies and rules. For example: block email containing sensitive keywords, stop uploading of a confidential document, detect screen capture, prevent the use of external drives etc. The templates cover virtually every use case of data loss prevention, insider threat detection and compliance requirements. Just pick a policy or rule template and all the data definition, content source, condition will be set automatically for you to edit.
Endpoint Data Loss Prevention & Egress Control
StaffCop helps you put exfiltration and egress controls in place to monitor and prevent illicit sharing of information. For example, File Transfer rules to block use of removable media. Clipboard rules to prevent sharing of confidential information like customer data outside the CRM. Network rules to restrict download/upload operations in the Cloud for certain file types or all files (no need for separate Cloud Access Security Brokers). Or use dedicated Application rules to limit or completely disable social media and IMs to prevent potential data leak by social engineering. There are hundreds of use cases where StaffCop can proactively defend your data from malicious or accidental leaks or misuse
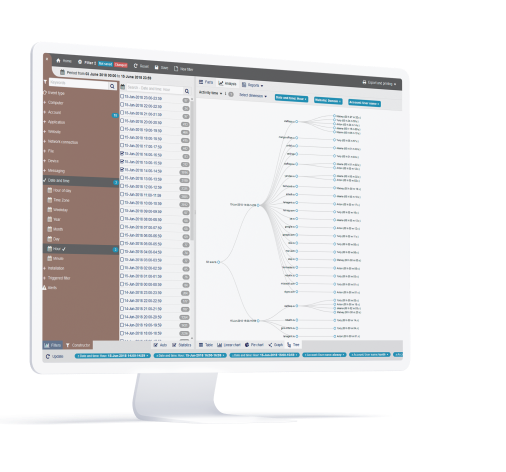
Behavioral Anomaly Detection
Define what constitutes dangerous or harmful user behavior and StaffCop's sophisticated anomaly engine will automatically detect when a user, department or group deviates from their normal parameters or exceeds acceptable risk levels. For example, get notified if a user sends too many attachments or prints more pages than normal. StaffCop can detect anomalies in applications, emails, network, file activities, printing and more. Immediately get notified about harmful user activity, lock out user or take remote control of the compromised system before any malicious or fraudulent attempts are made.
Privileged User and Third-Party Monitoring
StaffCop allows organizations to create profiles for privileged users, contractors and other third-parties and then define what information and system resources each profile can access. Further rules can be set up by behavior policies so that access to sensitive information is segregated by the organization’s security policy, or on a need-to-know basis. Rules can also be created to notify the authorities of any suspicious privileged user activity, such as unauthorized changes to system configuration, creation of backdoor accounts, unscheduled logins, a contractor trying to access restricted databases etc.

Security Sandbox
StaffCop allows you to create virtual servers on Windows, VMware Horizon etc. Utilizing this capability, you can for example, setup a Terminal Server for your partners, contractors or vendors . These external users can then login to the server using RDP keeping out of your internal network and repositories. At the same time, you can record their activates separately, restrict access or take control of the server in case of an incident keeping rest of your business immune to disruption.
Digital Forensics and Auditing
Detailed alerts for all users can be viewed including any security incidents and what actions were taken. Warning messages can be configured to inform the users about nonconformity and influence corrective behavior. Session recordings and history playback can be used to view user’s desktop for audit and evidence gathering purposes


Risk Assessment and Treatment
StaffCop has a dedicated Risk dashboard where the CSO and security analysts can conduct organization-wide risk assessment. Risk can be profiled by users, departments or by system objects. Reports can be derived by severity of risks or by how many times security violations occurred. Unique Risk Scores helps you identify high-risk users or policies so that plans can be developed for treating the risks.
Compliance Management
StaffCop comes with support for implementing compliance and standards like NERC CIP Standards for Electric Utilities, FISMA, FERC, ISO 27001, GDPR etc. Our flexible Policy and Rules Editor and powerful analytics and reporting features can help you develop your own organization-specific security and privacy, etiquette and acceptable use policies or conform with any regional data privacy and notification laws applicable to your organization.

Need a More
Comprehensive Solution?
Comprehensive Solution?

Information Security
Receive the required data “on the fly”. Search by keywords and regular expressions. Record sound from microphones to hear what was happening at the moment of interest.
Try for free 
Remote Administration
View remote desktop without being notices. Take control over a workstation. Full picture of software and hardware usage. Intensity of usage and registry of states..
Try for free Recommend

Employee Monitoring
Categorize applications and web-sites into productive and unproductive. Set up different configurations for particular users, groups and departments. Compare results.
Try for free Flexible Deployment Options

Bare Metal
Install on bare metal from our ISO image containing Ubuntu 18.04 and StaffCop or install StaffCop packages on existing Ubuntu 18.04.

Virtual Machine
Install on any OS as a virtual machine from our ISO image, use Virtual Box, VMWare, Hyper-V or any other virtualization system. Easy administrating without risking the host machine.

Private Cloud
Use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more
LEARN
Documentation SUPPORT
%201.svg?v=2020-10-15T10:37:02.579Z)




